Data Encryption for Organizations: A Strategic Defense with Utimaco Solutions
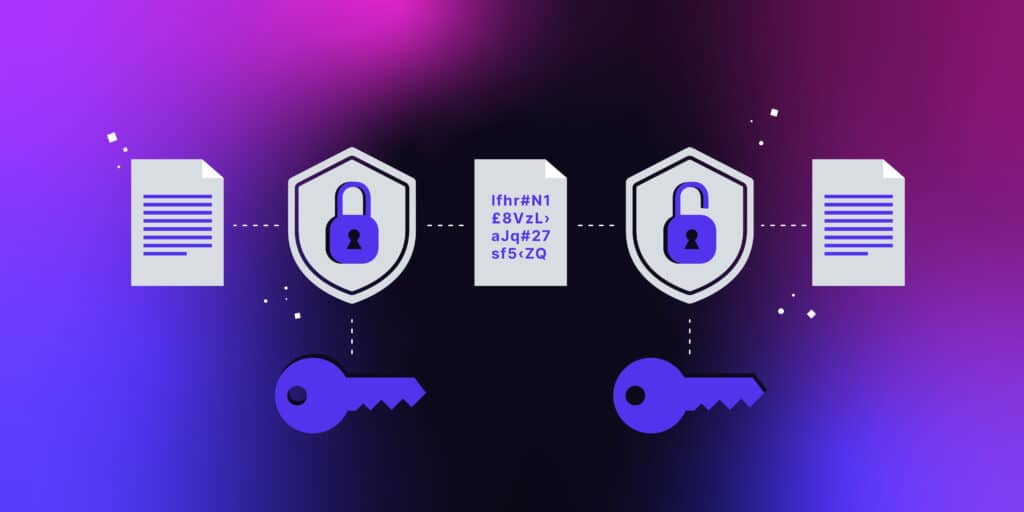
In a world where data breaches and cyberattacks are increasingly common, enterprises need a robust defense to safeguard sensitive data. Encryption serves as the last line of defense, ensuring that even if attackers bypass other security layers, the data remains inaccessible without proper authorization. This article delves into the importance of encryption, highlights its use in protecting data at rest and in motion, and explores how solutions like Utimaco provide comprehensive encryption capabilities, including file and folder encryption, public key infrastructure (PKI), hardware security modules (HSMs), and encryption key management.
The Importance of Encryption
Encryption is the process of converting plaintext data into an unreadable format, decipherable only by those with the appropriate decryption keys. As a critical component of cybersecurity, encryption addresses several key challenges:
- Data Breach Mitigation: Encrypting data ensures that it is useless to attackers even if they gain unauthorized access.
- Regulatory Compliance: Encryption is a mandatory requirement under many regulations, including Bank of Ghana Cyber and Information Security Directives, GDPR, PCI DSS, and HIPAA.
- Enterprise Trust: Securing sensitive data helps maintain customer confidence and prevents reputational damage.
Encryption at Rest
Encryption at rest protects data stored on physical or virtual media, including databases, hard drives, cloud storage, and file systems.
How It Works
Data is encrypted as it is stored, ensuring it is secure even if storage devices are lost or stolen.
- File and Folder Encryption: Solutions like Utimaco’s LanCrypt provide robust encryption for files and folders. Unlike traditional full-disk encryption, LanCrypt allows granular control, enabling enterprises to encrypt specific files or folders based on user roles, access levels, or organizational policies.
- Database Encryption: Protects sensitive data fields, such as customer records and payment information, in enterprise databases.
Key Features of Utimaco LanCrypt
- Centralized Management: Simplifies the encryption process by allowing centralized policy enforcement across multiple endpoints.
- Role-Based Access Control: Ensures only authorized users can decrypt and access specific files or folders.
- Compliance Enablement: Helps organizations meet compliance requirements for data protection by encrypting sensitive information.
Encryption in Motion
Encryption in motion secures data as it travels across networks, preventing interception or unauthorized access.
How It Works
Data transmitted between endpoints, such as servers, applications, or devices, is encrypted using secure protocols.
- TLS (Transport Layer Security): Protects web traffic, email communication, and API calls.
- Virtual Private Networks (VPNs): Manage encryption keys used on devices e.g Firewalls etc used to encrypt network traffic to ensure secure remote access.
- End-to-End Encryption (E2EE): Ensures that only the intended recipient can decrypt the data.
Utimaco’s Role in Securing Data in Motion
Utimaco’s PKI solutions play a critical role in securing data in motion. Public Key Infrastructure (PKI) enables the issuance, management, and validation of digital certificates, ensuring that communication channels remain secure.
Encryption Key Management
Encryption is only as strong as its secure key management. Secure storage, rotation, and lifecycle management of encryption keys are vital to ensuring the integrity of encrypted data.
Key Management with Utimaco
Utimaco’s Hardware Security Modules (HSMs) provide a secure and tamper-proof environment for key storage and management.
- Key Generation and Storage: HSMs generate and store encryption keys in a secure environment, preventing unauthorized access.
- Key Rotation and Expiry: Regularly rotating encryption keys enhances security, reducing the risk of key compromise.
- Integration with Applications: Utimaco HSMs integrate seamlessly with enterprise applications, databases, and file systems to enable strong encryption.
- Support for PKI: Utimaco HSMs are essential for managing digital certificates, ensuring secure authentication and communication.
Benefits of Utimaco HSMs
- Tamper-Resistant Design: Provides physical and logical protection for encryption keys.
- Compliance Support: Meets industry standards like FIPS 140-2 and Common Criteria, ensuring regulatory compliance.
- Scalability: Handles large volumes of cryptographic operations, making it ideal for enterprises of all sizes.
- Cost Effective: As compared to other OEMs, Utimaco is cost effective with a lower overall Total Cost of Ownership (TCO)
Encryption as a Last Line of Defense
While firewalls, intrusion detection systems, and endpoint protection controls form critical layers of enterprise security, encryption stands as the final barrier. If all else fails, encrypted data remains inaccessible without the appropriate keys, rendering it useless to attackers.
How Utimaco Strengthens Enterprise Encryption
- End-to-End Encryption: By combining solutions for data at rest (LanCrypt) and in motion (PKI), Utimaco ensures complete data protection.
- Integrated Key Management: Simplifies encryption workflows while enhancing security.
- Regulatory Readiness: Facilitates compliance with data protection regulations (Data Protection Act) through robust encryption practices.
Implementing Enterprise Encryption: A Strategic Approach
- Conduct a Data Classification Assessment: Identify sensitive data that requires encryption.
- Identify and document all the encryption use cases for the organization
- Adopt a Unified Encryption Strategy: Integrate encryption at both rest and motion to ensure end-to-end security. It is critical to centralize the management of encryption keys for all use cases (as much as possible) to simplify ongoing management.
- Leverage Strong Key Management Practices: Use hardware security modules (HSMs) and Key Management Systems (KMS) to manage and protect encryption keys.
- Train Employees: Ensure teams understand encryption’s role and follow security best practices.
- Regularly Update Encryption Protocols: Stay ahead of evolving threats by using the latest encryption standards. (Quantum Ready algorithms will soon become standard)
Conclusion
Encryption is no longer optional—it is a business imperative. With the increasing frequency of cyberattacks and stricter regulatory requirements, enterprises must adopt a holistic encryption strategy. Solutions like Utimaco LanCrypt and HSMs empower organizations to:
- Protect sensitive data at rest and in motion.
- Securely manage encryption keys and digital certificates.
- Meet compliance requirements with confidence.
By incorporating encryption as the last line of defense, enterprises can ensure that their data remains secure, even in worst-case scenarios. As businesses evolve, encryption solutions like those offered by Utimaco will continue to be indispensable in safeguarding enterprise data and preserving trust.

0 Comments